Enhance Threat Detection with Vectra XDR and CrowdStrike Falcon LogScale
Vectra XDR generates a constant stream of audit, detection and scoring events as it tracks behavior across cloud, identity and network surfaces. Left as raw JSON these logs are hard to normalize and even harder to use during a live incident. When LogConnector streams that telemetry into Falcon LogScale with a dedicated parser and dashboards, your analysts get clean fields, fast queries and views that actually explain what Vectra is seeing.
Vectra XDR focuses on AI driven threat detection and response across cloud, identity and network environments. That power comes with a cost. The raw logs are rich but noisy, and without structure security teams spend more time wrangling data than validating threats. The Vectra XDR package for Falcon LogScale solves that problem by turning detection streams into normalized, query ready events you can pivot on, correlate and visualize.
Vectra XDR parser
At the center of the package is the vectra-xdr parser. It takes unstructured Vectra XDR logs and turns them into clearly categorized events that are easier to search and correlate in real time. The parser understands the key Vectra event families so you can work with them directly inside Falcon LogScale instead of digging through nested structures.
- Supports multiple log types including audit events, detection events, entity scoring events and supporting telemetry from cloud and identity sources.
- Normalizes core fields such as account, host, entity, detection category, severity and confidence so filters and alerts can be reused across dashboards and searches.
- Enriches detection logs with MITRE ATT&CK technique details, giving analysts instant context on what type of behavior is being observed and how it maps to standard frameworks.
Dashboards overview
To complement the parser, the package includes a small set of purpose built dashboards that line up with how analysts already think about XDR activity. Each view is tuned for quick triage and can be adapted to your own scoring thresholds and response flows.
Key dashboards in the package:
- ✓Audit views that show configuration changes, account updates and integration activity so you can spot risky shifts in the platform itself.
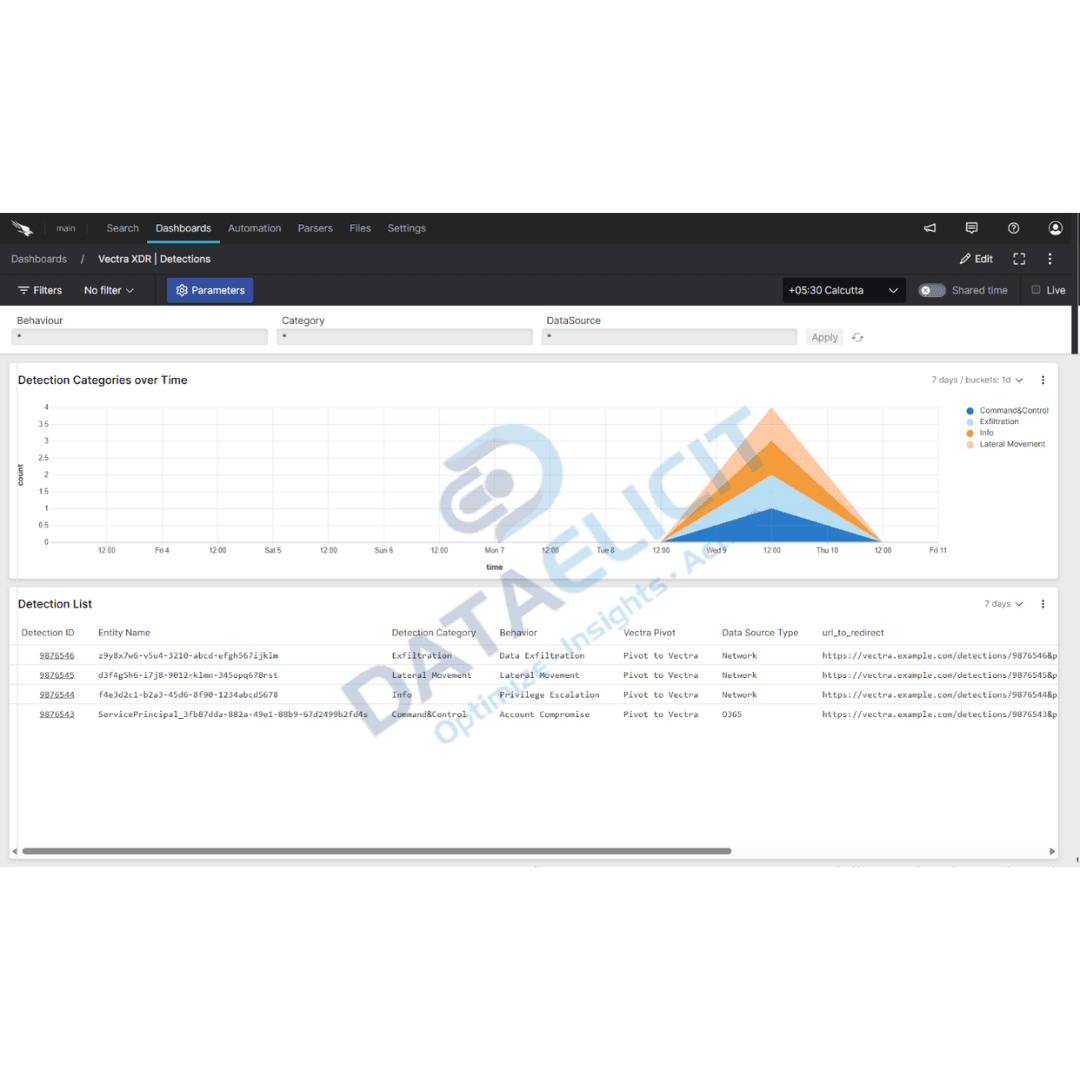
- ✓Detections dashboards that break down alerts by category, severity, data source and ATT&CK mapping for fast triage and prioritization.
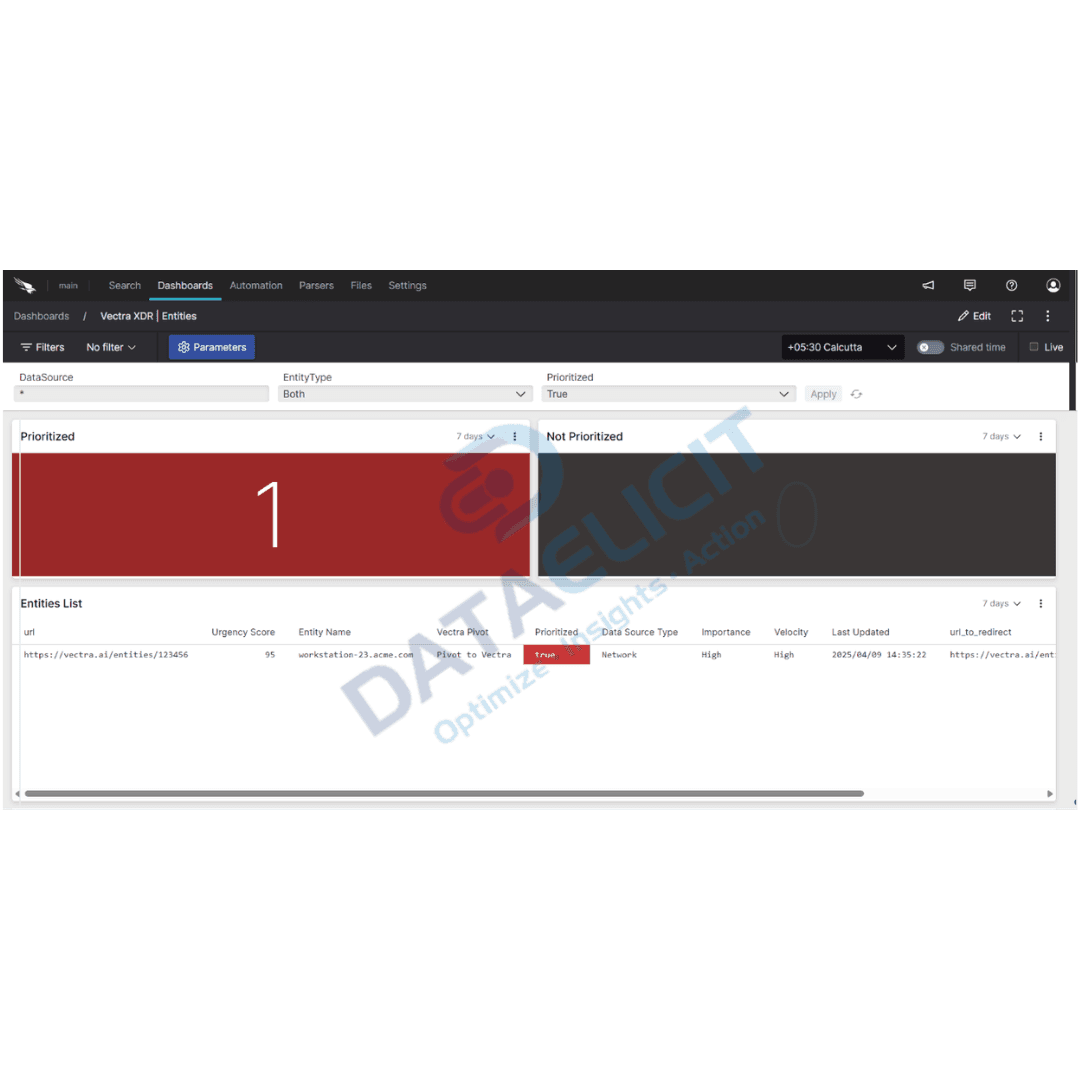
- ✓Entities views that track high scoring hosts, users and workloads over time so patterns of risky behavior are obvious instead of buried.
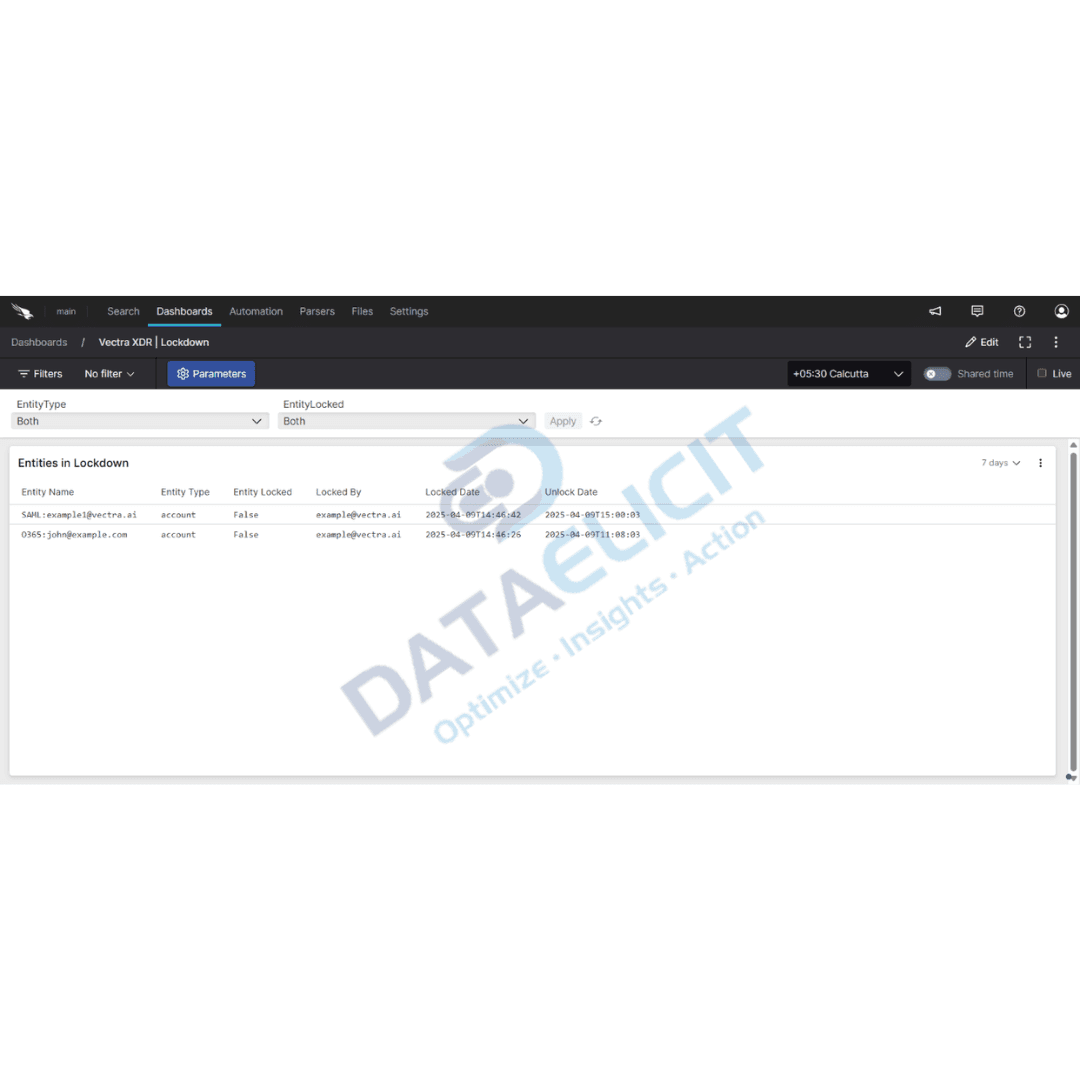
- ✓Lockdown style panels that help you validate containment and response by correlating detection timelines with follow up activity.
These dashboards are aimed at SOC analysts and incident responders who need visibility without wading through raw log dumps. They give a fast path to suspicious activity, help prioritize work and provide clean visuals for post incident reviews.
Why this matters
Many teams already rely on Vectra XDR but still export CSV slices or screenshots when an investigation heats up. That slows everything down and hides context that LogScale can surface in a few seconds. With structured Vectra events in Falcon LogScale you can correlate detections with identity, endpoint and network data, prove which entities are actually at risk and push that insight into response playbooks.
Conclusion
The Falcon LogScale package for Vectra XDR delivers faster threat detection and deeper visibility by combining structured parsing, MITRE ATT&CK mapping and focused dashboards. Whether you are responding to a high priority alert or monitoring your environment more broadly, this integration gives your team the context and speed required to respond with confidence.
Alongside this package, LogConnector acts as the bridge between your data sources and Falcon LogScale. It removes ingestion complexity and lets you reuse the same patterns for other security tools, so Vectra XDR becomes part of a wider, consistent analytics stack instead of another silo.
Ready to dive deeper?
In real projects we help customers decide which Vectra scopes to ingest, how to balance data volume against retention and how to align XDR dashboards with existing SOC workflows. The goal is a setup that exposes real risk without turning every burst of telemetry into a cost problem.
Get in touch with us today
We work with security, platform and operations teams that want Vectra XDR detections to land in a place where they can be searched, correlated and reported on without friction. That usually means tighter investigations, cleaner evidence for incident reports and less time copying charts between tools.
Once ingestion, parsing and dashboards are tuned, you can track practical outcomes like reduced time to validate alerts, better coverage of high value entities and clearer reporting to leadership on where risk is trending.
Talk to the team
Want Vectra XDR insights to land where your analysts live?
We design and support LogConnector pipelines that bring Vectra XDR data into Falcon LogScale with tested parsers, dashboards and alerting approaches that match your environment.
Get in touch with us today
to learn more about:
- ›LogConnector features and benefits
- ›Vectra XDR package for Falcon LogScale
- ›How LogConnector and Falcon LogScale can enhance your IT and security operations
Related Articles
Explore more guides where LogConnector streams security and observability data into Falcon LogScale with normalized fields and ready to use dashboards.